CertiK: The Pursuit of Securing the Web3 World
Delve into the CertiK Project, an in-depth analysis of cutting-edge blockchain security solutions. Discover how CertiK's innovative technology safeguards against threats, mitigates risks, and enhances blockchain security.

1. Overview
Smart contracts represent a significant departure from traditional centralized information systems, as they rely on the trustworthiness of code rather than the integrity of corporate actors. On Web3, billions of dollars can be managed solely by lines of code. This gives rise to Cryptosecurity —a sector involving technologies that help secure digital wallets and cryptocurrency transactions. As Web3 is rapidly growing, so does security providers need to mitigate and moderate the looming risks in this highly decentralized space.
This article will delve into CertiK. From that, we can understand its paramount role in empowering and helping projects navigate the myriad challenges of Web3 Security.
1.1 Brief history
CertiK is a prominent security provider within the Web3 ecosystem, established in 2017 by a team of computer science specialists from Yale and Columbia University. The company's core objective is to enhance the security and reliability of the blockchain industry by offering premium security services to blockchain projects of various scopes and scales.
1.2 Trusted by the Best
CertiK is trusted by some of the biggest names in the blockchain industry including Binance, the Sandbox, TON, and Polygon. With its reputation for excellence and cutting-edge technology, CertiK is the go-to security provider for blockchain projects of all sizes. This goes without saying, CertiK is also trusted by some of the most prominent investors namely Sequoia, Goldman Sachs, InsightsPartners, and many more.
1.3 Key Services Offered by CertiK
CertiK offers a full suite of services to level up the security well-being of Web3 projects. Some of their key services include:
- Web3 Security Auditing: This audit features both Smart Contract and L1 Chain Audit ensuring they are secure and free of vulnerabilities. Their methods include a combination of formal verification and runtime verification to identify potential weaknesses in the code and provide recommendations on how to address them.
- Penetration testing: CertiK's penetration testing service is designed to identify potential vulnerabilities in a blockchain project's infrastructure and network. They use various tools and techniques from black hat hackers to simulate real-world attacks and provide recommendations on improving security.
- Network monitoring: This is offered through Skynet and 24/7 incident response to protect against active threats.
- Advisory Services: CertiK offers compliance consulting and due diligence services to help blockchain projects comply with regulatory requirements. Their team of experts has extensive experience in blockchain compliance and can help projects navigate complex regulatory environments.
2. CertiK’s Auditing Methodology
When it comes to security there should be no compromise. The CertiK team ensures this through a combination of leading technologies and a rigorous auditing process in their services combining both manual review and automated tools.
2.1 Process Overview
CertiK’s audit process commences with the acquisition of the source code and the establishment of a tailored environment. Before delving into the utilization of in-house tools and manual examination to uncover any security vulnerabilities and design defects, the project documentation is examined by auditors who also perform threat modeling. Upon the completion of the audit, a detailed report containing the findings and recommendations is presented to the client.
2.2 Key Components Review
Environment Setup: Certik’s support extends to over ten major blockchain ecosystems and smart contract programming languages. They utilize pre-configured virtual machine environments to mitigate complications in the set-up process caused by some other languages. Any code added to these environments undergoes thorough examination for successful compilation and deployment capabilities. The environment equips auditors with the ability to execute code and carry out tests, enabling them to gain a practical comprehension of the project.
Architecture Review: Determining a project's architecture is crucial for effective threat modeling and understanding security-critical components. While it is ideal for clients to provide detailed documentation describing the architecture, there may be instances where auditors need to perform architecture extraction due to the absence of these artifacts. This involves examining component interactions, external inputs, code compliance, and concurrency, among others. Visualization tools can aid the process, but poorly organized or unconventional projects may necessitate manual analysis. It's also essential to identify if a project is an original design or a fork, as forks may inherit vulnerabilities from the original project.
Threat Modeling: A Threat Model represents a system's critical assets, resources, security requirements, vulnerabilities, and threats. It's established during an architecture review by posing and answering questions based on the system's architecture. The Threat Modeling process produces a security checklist for the security audit and ensures a thorough evaluation of the system's security posture.
Static Analysis & Formal Verification: CertiK’s in-house tools draw on their extensive experience and database of over 60,000 findings from 3,500+ audits and incidents. By testing code statically at the source code and bytecode levels, they can identify insecure code patterns and generate diagrams to enhance smart contract visibility. The tools' efficacy improves with each audited project, and CertiK also provides formal verification to ensure program specifications are met. Formal verification mathematically proves a program's intended function by expressing its properties as formulas and using automated tools to check its veracity. Findings typically include logic issues, reentrancy risks, and lack of access controls. Manual verification by auditors removes false positives and enhances result clarity.
Reporting & Remediation: CertiK’s audit reports are comprehensive and provide a thorough analysis of a project's security posture, beginning with an overview of the project's type, ecosystem, and scope. The reports include an appendix that defines our security ratings and terminology, as well as detailed descriptions of our methodology and auditing approach. They also provide specific testing information, including formal verification processes and their results.
The findings include detailed explanations of identified issues, with metadata such as category, severity, file location, and alleviation status. Each finding is divided into four sections: Description, Scenario, Proof of Concept, and Recommendation. These sections provide targeted and actionable information to improve readers' understanding of the findings.
The remediation phase is an ongoing dialogue between the client and CertiK’s auditors to improve the project's security. The client receives the initial security assessment and provides updated source code or comments. Then auditor updates the findings accordingly and publishes an updated report. This process repeats until the client is satisfied with the final security assessment. Their reports are published to clients and publicly available on the Security Leaderboard, allowing community members to view how projects improve their security ratings using CertiK audits and security services.
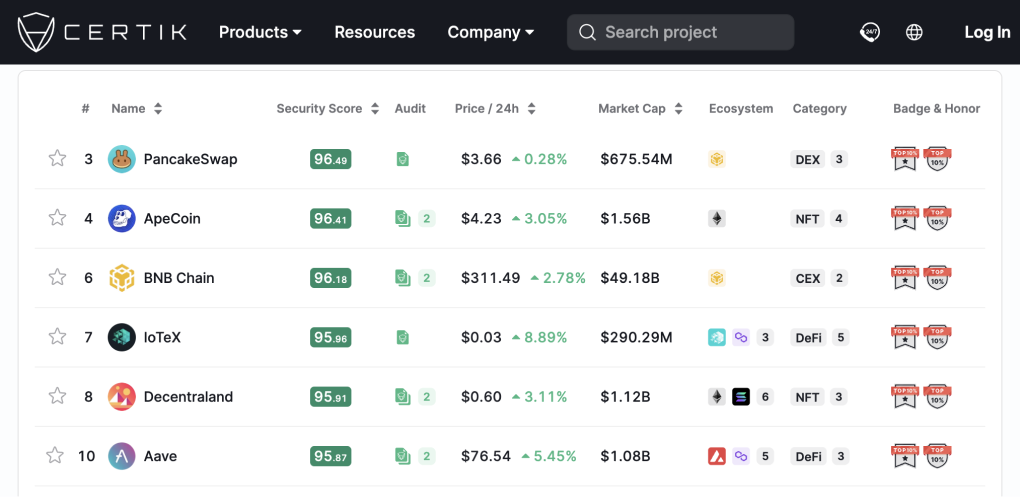
3. Skynet: Built for both Community & Businesses
CertiK’s products & services are standing out as they strike the balance between fostering Community trust while effectively serving Web3 Projects. This is where Skynet comes in with both offerings for the community and businesses.
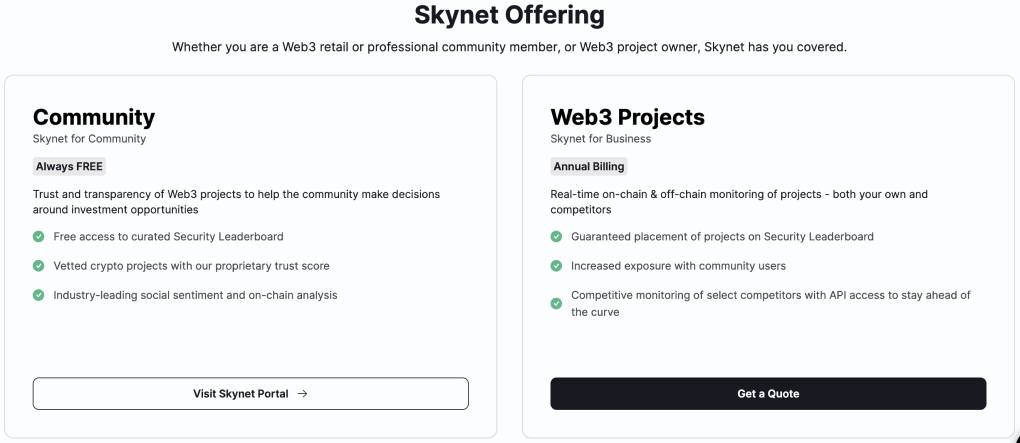
Skynet for community: It is an integrated platform that offers security, due diligence, and insights capabilities, with the goal of promoting trust and transparency in the Web3 ecosystem. The platform has been designed to provide users, investors, and project teams in the community with the necessary resources and tools to navigate the Web3 space with confidence. Skynet for Community allows users to conduct in-depth due diligence using relevant on-chain and social data, explore newly audited projects, and access valuable industry insights and best practices, all through a single user-friendly platform.
One of the most outstanding features of Skynet is the security scores for Web3 projects. The score is calculated by aggregating sub-scores from different signals, where a higher score indicates better performance in specific security measurements. CertiK integrates over 15 signals that measure security performance across six security categories: Code Security, Fundamental Health, and Operational Resilience. Community Trust, Market Stability, Governance Strength.
New and improved Security Scores for 10k+ projects!
— CertiK (@CertiK) April 3, 2023
15 signals that measure security performance across six security categories 👇
1⃣Code Security
2⃣Fundamental Health
3⃣Operational Resilience
4⃣Community Trust
5⃣Market Stability
6⃣Governance Strengthhttps://t.co/iWCqHeQCvR
Skynet for Business: It is built to address the specific needs of Web3 Projects for end-to-end security and brand monitoring system. The package features proprietary data insights and a security alert platform for Web3 projects and their communities.
4. Successful Stories
With more than 3,700 clients have been relying on CertiK’s auditing solution, CertiK can easily boast a long list of successful audit stories. There are three outstanding cases that are worth mentioning.
CertiK X Aptos: Aptos gains a comprehensive defense-in-depth security approach through CertiK's Security Suite. CertiK’s suite provides a range of security solutions from pre-deployment auditing to continuous post-deployment monitoring using blockchain analytics tools like Skynet. By partnering with CertiK, Aptos can prioritize security in the development process and better protect its community and ecosystem. CertiK has an unparalleled understanding of building on this novel Layer One, and its tools are designed to keep pace with rapid growth.

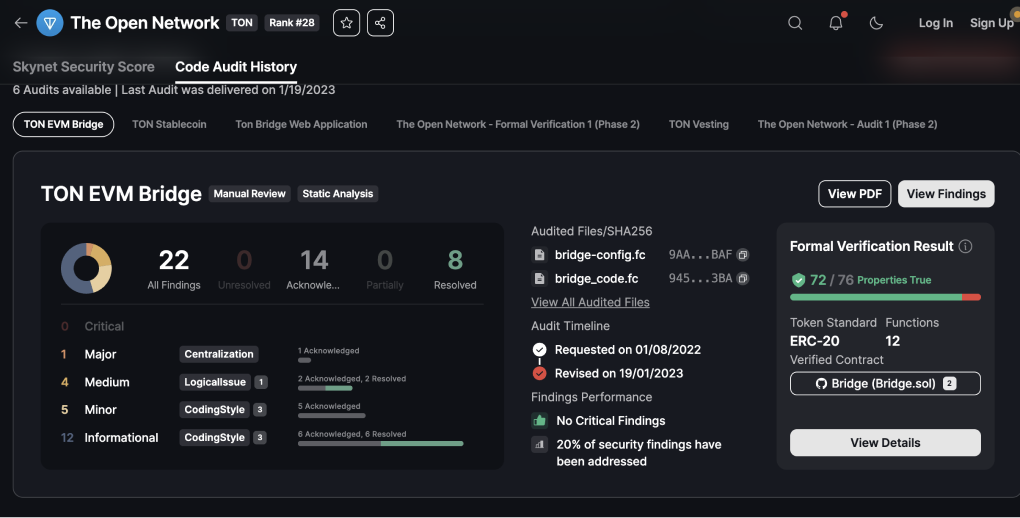
CertiK X TON: CertiK audited several crucial aspects of The Open Network, such as vesting schedules, the TON bridge application, the TON baselayer, and other contracts in development. Formal verification was also used to provide an extra layer of security to the network. By combining manual review with automated, and AI-powered verification, CertiK adopts a defense-in-depth approach that safeguards against the actual risks that come with the Web3 world.
CertiK X Community: CertiK's Skyfall team conducted a thorough review of many mobile wallets and found that ZenGo's MPC solution provides stronger security defenses than regular mobile wallets. In particular, ZenGo's wallet can defend against direct attacks from privileged attackers. However, defending against privileged attackers is challenging. CertiK’s review presents a new attack vector that is orthogonal to the MPC method in ZenGo. They reported the security issue and ZenGo made a prompt response to fix this issue.
When the leading #blockchain #security firm @CertiK reviews your wallet and concludes:
— ZenGo Wallet (@ZenGo) April 4, 2023
"ZenGo's security practices demonstrate a comprehensive approach to protecting users, surpassing those of many regular wallets on the market today."
Join us for a discussion ⬇️ https://t.co/PQHour603H
5. The Future of Web3 Security
5.1 Challenges
Earlier mentioned in our article on the importance of Security and RegTech, the success of Web3 relies heavily on how it remedies emerging risks and improves security with innovative solutions. Web3 technology introduces new challenges for security compared to its predecessor, Web2. While decentralization can address power asymmetry, control, censorship, fraud, and privacy risks, it can also lead to new risks in data security, identity, economic incentives, and novel approaches to social engineering. Therefore, it is crucial to incorporate security-by-design principles, including minimizing attack surface areas, securing defaults, and zero-trust, into Web3 systems. A defense-in-depth approach that combines expert manual review with automated, AI-powered verification can also mitigate and protect against the risks inherent to the Web3 world.
5.2 How CertiK is positioning itself?
Security runs deep within CertiK’s DNA. Security takes in form of everything that shapes up CertiK - an industry leader in Web3 security & auditing solution. They achieved this by leveraging not only blockchain technology but also AI technology to enhance their security audit. In addition, CertiK also emphasizes its team of security experts who are equipped with the latest tools and techniques to provide comprehensive security audits.
Above all, CertiK stands out thanks to its community-focused approach to security. They foster the community’s trust by making audit reports publicly available. They build free and easy-to-use analytical tools to empower the community to carry out and conduct a thorough analysis, thus raising the overall security standards of Web3.
5.3 How NodeReal will support here?
NodeReal specializes in providing a reliable and secure infrastructure for blockchain and decentralized applications. NodeReal can provide comprehensive data service like RPC APIs to not only CertiK but also their clients, effectively upgrading not only security standard but also node infrastructure standard across Web3.
DeFi is getting more traction and popoluarity so does its risks are looming larger. As a guardian of Web3 Security, CertiK can leverage NodeReal’s DeFi API such as PanCakeSwap GraphQL API to supercharge CertiK’s existing product suite. Skynet is the case in point where it can be supercharged to upgrade its liquidity monitor feature.
NodeReal’s Application Chain Solution can also offer great benefits for a Web3 security provider like CertiK. The customization feature of Appchain ie customized consensus mechanisms and smart contract rules for each sidechain enable CertiK to advance its formal verification feature. Additionally, AppChain's architecture allows for faster detection and resolution of security breaches, as any issues occurring in a sidechain can be isolated and addressed without affecting the main blockchain, ensuring the overall integrity and security of the dApps ecosystem.
6. Conclusion
Security is undoubtedly one of the most important factors in the success of a Web3 Project. It should never be compromised as a single vulnerability can mark the demise of the most promising project. With more than $360 billion of secured market capitalization across over a dozen blockchains, CertiK-audited projects have been shaping the future of Web3. As the innovation and potential of Web3 lie in the interoperability trend, a security-focused approach will ensure the long-term growth of newly built projects and protocols. With that note, we believe Certik is here to stay for the thrive of Web3 security and NodeReal is happy to be a part of this journey with Certik.
About NodeReal
NodeReal is a one-stop blockchain infrastructure and service provider that embraces the high-speed blockchain era and empowers developers by “Make your Web3 Real”. We provide scalable, reliable, and efficient blockchain solutions for everyone, aiming to support the adoption, growth, and long-term success of the Web3 ecosystem.
Join Our Community
Join our community to learn more about NodeReal and stay up to date!

